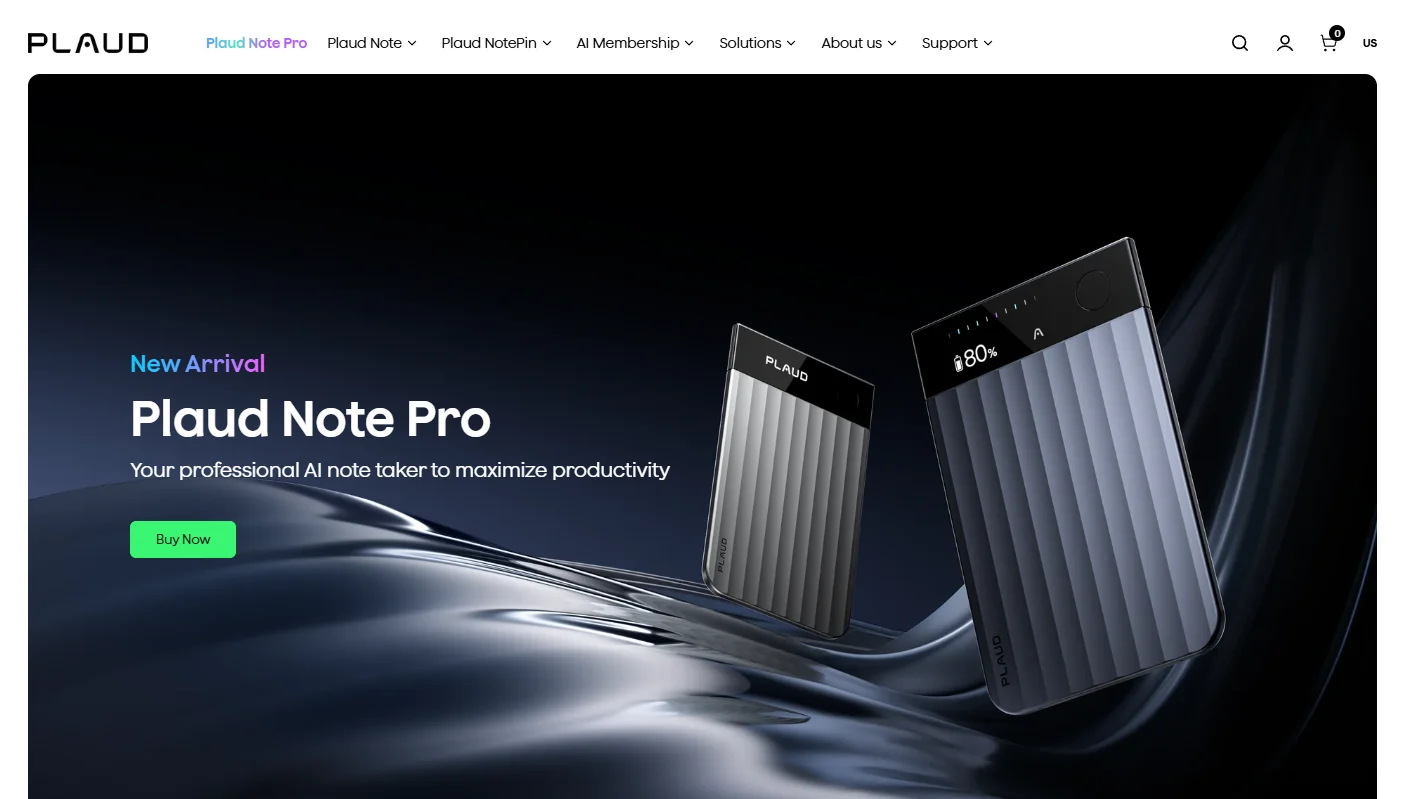
More browsers are experimenting with agent capabilities that can perform actions on behalf of users—such as booking tickets or making purchases—but these features also introduce security risks that could lead to data breaches or financial loss.
Google has outlined its approach to safeguarding users in Chrome through an observer model and explicit user consent for agent-initiated actions. The company previewed Chrome’s agent functionality in September and indicated that it will roll out broadly over the coming months.
According to Google, it employs several models to govern agent behavior. Specifically, it leverages Gemini to build a user-aligned “critic” model that reviews action plans generated by the planning model for a given task. If the critic determines that the proposed actions don’t align with the user’s intent, it prompts the planner to revise its strategy. Notably, the critic only accesses metadata about the proposed actions—not the actual webpage content.
To further restrict agent access to unauthorized or untrusted sites, Google implements an “agent source set,” which limits interactions to designated read-only and read-write sources. Read-only sources include data Gemini is permitted to extract—such as product listings on a shopping site—while irrelevant elements like banner ads are excluded. Similarly, agents are only allowed to click or input data within specific iframes on a page.
“This segmentation ensures that agents only have access to data from a constrained set of sources, and that this data is only shared with authorized write destinations,” the company explained in a blog post. “It also enables the browser to enforce isolation—for example, by not sending data outside the approved read set to the model.”
Google also uses a separate observer model to inspect URLs during page navigation, helping block access to potentially harmful, model-generated links.
The search giant emphasizes that users retain control over sensitive operations. For instance, when an agent attempts to navigate to sites containing banking or medical information, Chrome first seeks explicit user approval. For login-required sites, it asks whether the user permits Chrome’s password manager to autofill credentials—though the agent model itself never accesses password data. Additionally, user confirmation is required before actions like purchases or message sending are executed.
Beyond these measures, Google has implemented a prompt injection classifier to block unintended operations and is actively testing the agent feature against adversarial attacks crafted by security researchers.